What makes Swiss cloud security different?
Swiss cloud security prioritizes data sovereignty, legal certainty, and operational control. Learn how cloud platforms in Switzerland compare to multinational public cloud platforms.
Swiss cloud security prioritizes data sovereignty, legal certainty, and operational control over global scale and convenience. For organizations evaluating cloud security in Switzerland, this difference has direct implications for compliance, risk exposure, and long-term accountability.
In simple terms, secure cloud services in Switzerland are built for businesses that can’t afford uncertainty around where their data lives, which laws apply to it, and who ultimately controls access.
Data sovereignty is the foundation of Swiss cloud security
Data sovereignty determines which legal system governs your data, not just the servers' physical location.
In a Swiss cloud environment:
- Data is physically hosted in Switzerland.
- Swiss law governs access, disclosure, and oversight.
- Foreign authorities don’t have the right to compel access without a Swiss legal process.
This is a critical distinction.
Many public cloud platforms offer regional hosting, but the provider itself may still fall under foreign jurisdiction. Local hosting doesn't always mean local legal control.
For example, U.S. courts can subpoena data hosted in Europe, but the process and legality depend on whether the entity holding the data is a U.S.-based company or a foreign organization.
Recent court cases show that there is still ongoing conflict between U.S. discovery orders and European privacy laws.
1. Eaton Corporation (2025)
In a major case testing European privacy laws, the U.S. District Court for the Northern District of Ohio ordered Eaton Corporation to produce employee performance reviews stored on servers in Dublin, Ireland.
Eaton argued that compliance would violate the General Data Protection Regulation (GDPR). The judge conducted a “comity analysis” and determined that the Internal Revenue Service’s audit interest outweighed the employees' privacy concerns, especially since the data was corporate and not "special-category" (sensitive) personal data.
2. Congressional subpoenas to tech giants (2025)
House Judiciary Chair Jim Jordan subpoenaed eight U.S. tech giants, including Microsoft, Alphabet, and Meta, over their communications with foreign governments, specifically about compliance with EU and UK regulations.
This highlights how U.S. legislative subpoenas are increasingly targeting data related to European regulatory compliance.
3. Latombe v. Commission (2025)
While not a direct subpoena case, the Latombe v. Commission ruling forms the basis for how data moves. The EU General Court upheld the EU-U.S. Data Privacy Framework (DPF), rejecting a challenge that U.S. surveillance practices lacked adequate safeguards.
This provides a more stable legal basis for U.S. courts to request data, as it recognizes U.S. protections as "substantially equivalent" to those in the EU.
Key legal instruments at play:
- The CLOUD Act remains the primary tool for U.S. authorities to access data stored in Europe by U.S.-based providers.
- Under the U.K.-U.S. Data Access Agreement, the U.K. has transmitted over 20,000 orders to U.S. companies seeking data access, serving as a model for future EU-U.S. agreements.
- The new rules of the EU Data Act, which took effect in September 2025, create additional obligations for U.S. tech companies to facilitate data porting while strictly regulating the transfer of data to non-EU authorities.
Swiss cloud security ensures that Swiss law, not foreign law, decides who can access your data.
Swiss data protection laws shape cloud security by default
Switzerland has a long-standing reputation for privacy and confidentiality, and is at the core of how Swiss cloud providers design their services.
The New Federal Act on Data Protection (nFADP) features several key elements:
- Strong alignment with GDPR requirements.
- Clear accountability for data controllers and processors.
- Proportionate, purpose-driven data handling
- A legal culture that treats privacy as a baseline, not a feature.
As a result, Swiss data protection in cloud environments is embedded into operations from the start rather than layered on later.
For regulated industries, this legal clarity often matters as much as technical security controls.
Swiss cloud vs public cloud security: control vs abstraction
The difference between Swiss cloud security and public cloud security isn’t primarily about technology. It’s about responsibility.
Public cloud platforms rely on highly abstracted shared-responsibility models. But in practice, this can blur:
- Ownership of security configuration
- Boundaries of compliance responsibility
- Incident response accountability
Swiss cloud providers typically offer:
- Clearer responsibility separation
- Greater infrastructure transparency
- Direct operational oversight
- Fewer opaque service dependencies
This approach reduces the risk of misconfiguration and shortens response times during security incidents.
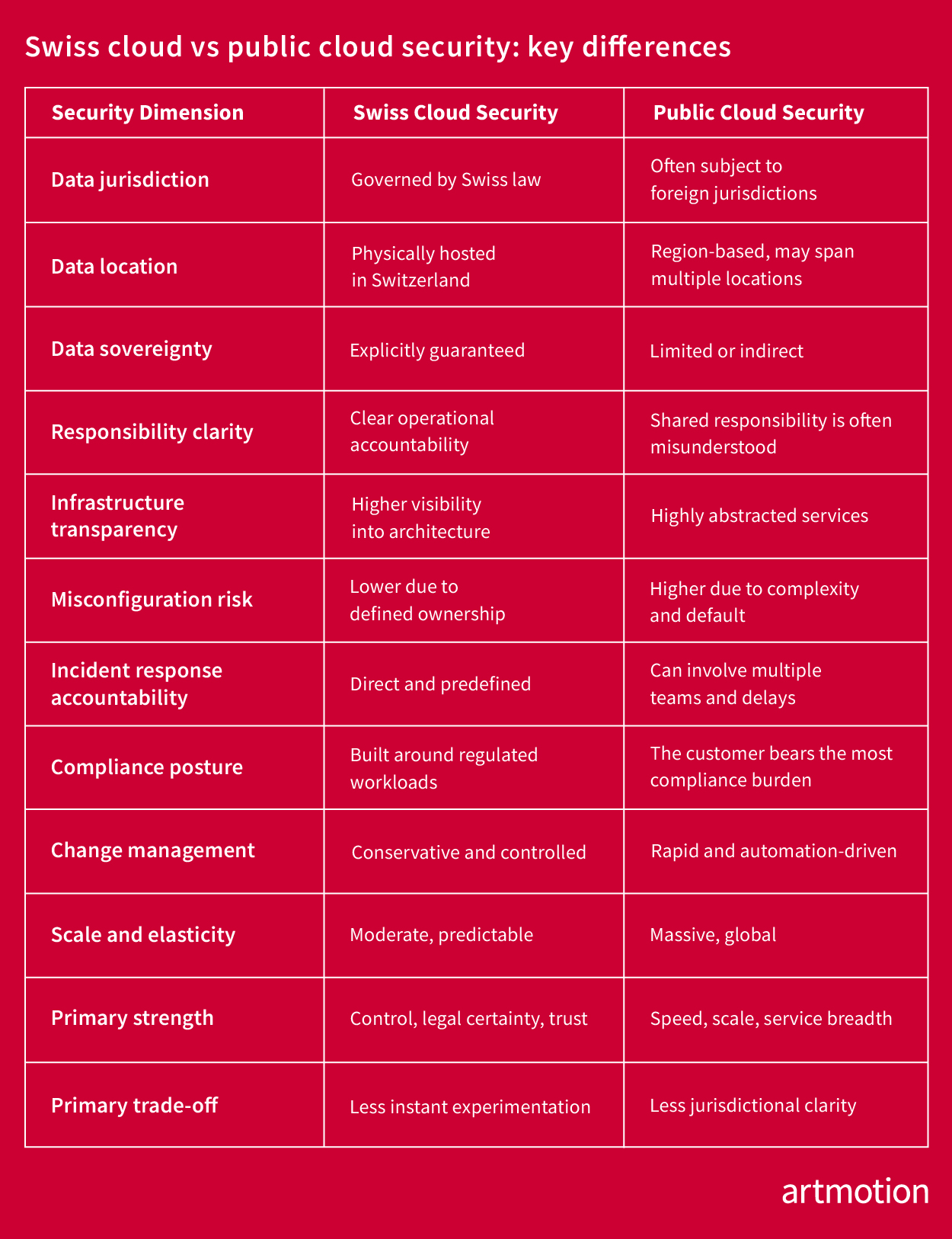
Figure 1: Swiss cloud vs public cloud security: key differences
Why Swiss cloud security favors control over scale
Global public cloud platforms are engineered for hyperscale. Swiss cloud security is engineered for predictability and control.
This difference shows up operationally:
- Smaller, more manageable attack surfaces.
- Conservative change management.
- Tighter access controls.
- Human oversight, where full automation introduces risk.
Most security failures don’t stem from a lack of tools. They stem from complex systems that no one fully controls. Swiss cloud security deliberately limits that complexity.
Built for security and compliance-driven organizations
Switzerland designs cloud security services for everyone. But they are ideal for organizations with strict regulatory or contractual requirements, including:
- Financial services
- Healthcare and life sciences
- Legal and professional services
- Public sector institutions
- Enterprises handling sensitive intellectual property
In these environments, auditability, access traceability, and data locality are architectural requirements, not optional add-ons.
Alternatives vs trade-offs: when Swiss cloud security is not the best fit
Swiss cloud security is a deliberate choice. It isn’t universally optimal. You have to consider multiple variables, including your business requirements, industry regulations, and scaling.
Public hyperscale cloud platforms
Best suited for rapid global scaling, worldwide latency optimization, and fast experimentation.
Trade-offs: foreign jurisdiction exposure, complex shared responsibility models, and limited operational transparency.
On-premises infrastructure
Best for complete physical control and legacy environments.
Trade-offs: higher operational overhead, slower scalability, and increased internal security burden.
EU-based cloud providers
Best for GDPR-aligned EU workloads.
Trade-offs: EU jurisdiction prevails over Swiss law, and legal access models differ.
In practice, many mature organizations adopt a hybrid approach, using hyperscale platforms for elasticity and Swiss cloud security for sensitive or regulated workloads.
The role of managed cloud security services in Switzerland
Secure infrastructure alone isn’t enough. To be effective, Swiss cloud environments require continuous security monitoring, robust encryption, threat detection and incident response, configuration oversight, and identity and access governance.
They should also leverage ethical hacking, including cloud security testing, penetration testing, and IT infrastructure testing.
Managed cloud security services in Switzerland connect secure architecture with real-world threat activity by providing ongoing visibility, response, and accountability.
Is Swiss cloud security more secure than public cloud?
Short answer: not in every scenario.
Swiss cloud security isn’t inherently more secure across the board. What it offers is stronger data sovereignty, greater transparency in legal accountability, and greater operational control.
For organizations with compliance-heavy or privacy-sensitive workloads, these factors often outweigh the benefits of hyperscale convenience.
Swiss cloud security prioritizes data sovereignty, legal certainty, and controlled infrastructure over convenience-driven scale.
Final thoughts
Swiss cloud security doesn’t aim to impress with size or speed. Instead, it seeks to withstand scrutiny.
By prioritizing jurisdictional clarity, accountability, and controlled infrastructure, Swiss cloud providers offer a model suited to organizations that can’t afford surprises. That’s what makes Swiss cloud security different.